Five Steps to Protect Your Critical Data From Insider Threats
- by 7wData
As companies around the world turn their attention to advanced threats endangering their most sensitive data, one category is commanding much-deserved attention: insider threats. With 44.5 percent of attacks perpetrated by malicious insiders, guarding against these incidents is becoming a pressing concern.
An effective way to tackle insider threats is with an integrated approach that accomplishes two related goals. First, organizations need to reduce their exposure to insider threats by securing their critical data and governing their identities. Second, they need to monitor the actions of their authorized users to detect any anomalous behavior using security intelligence. In this post, we will focus on the first piece of that integrated approach: securing sensitive data.
To protect an Organization’s most sensitive data, it is important to have a mature data security strategy in place. That strategy will help determine who owns the data, where it originated, how sensitive is it, what it can be used for and so on.
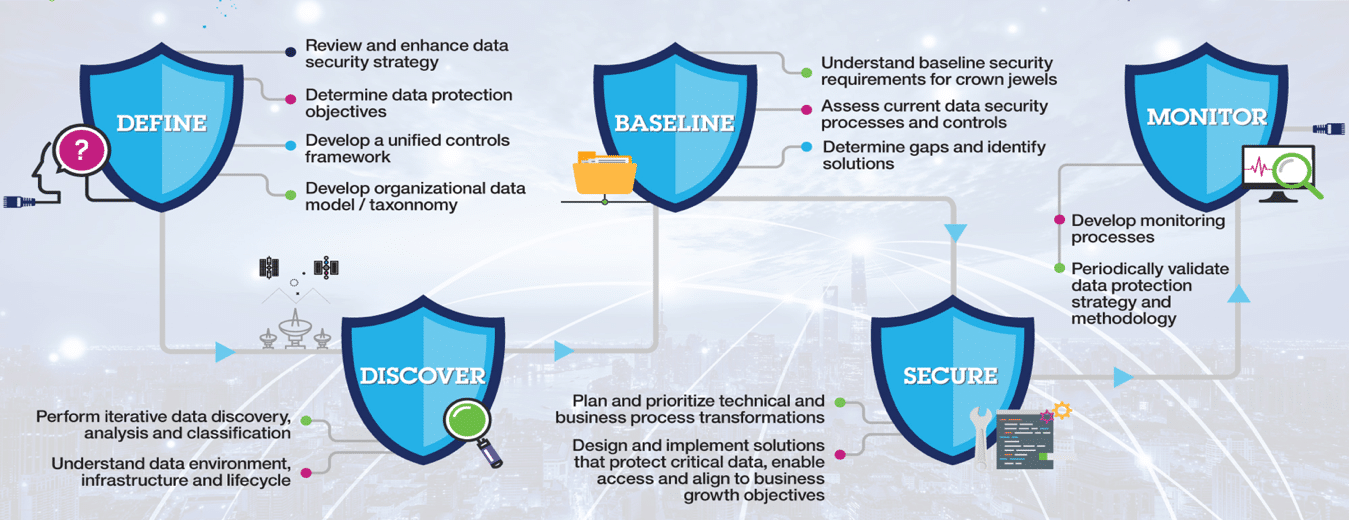
Organizations can follow a systematic, five-step approach to protect their data with the highest business value, commonly known as crown jewel data, as depicted below:
Taking time to understand the Organization’s strategic goals and how data security fits into these goals will provide guidance to the overall data security program. The initial phase of the five-step approach should focus on assessing the organization’s goals and objectives and ensuring appropriate policies and standards are in place. Stakeholder interviews, reviews of data management policies and standards, and any other relevant existing documentation should be included in the assessment to understand the current capabilities.
As part of this phase, it is also important to obtain agreement among the various IT and business stakeholders on what the critical data is, the impact that data has to the organization if it is lost and the required security control baselines to protect that data.
Knowing where your critical data is located within the organization is an important step to ensure it is adequately protected with multilayered security controls. Without having an understanding of where the critical data is stored, any security controls will have to be implemented across all systems, no matter if the system contains critical data or not, and that is not cost effective.
Once the organization’s current data environment is understood, a data discovery should be done across the organization’s structured and unstructured repositories to identify and classify critical data stored within those repositories. As these discovery results are gathered, a data catalog and taxonomy should be created to manage the findings.
[Social9_Share class=”s9-widget-wrapper”]
Upcoming Events
Shift Difficult Problems Left with Graph Analysis on Streaming Data
29 April 2024
12 PM ET – 1 PM ET
Read MoreCategories
You Might Be Interested In
Customers taking back control of their data from the Banks
25 Apr, 20172018 is likely to be a game-changing year for the banking and finance sector. As the General Data Protection Regulation …
Google got 1.6m patients’ data ‘inappropriately’
18 May, 2017Google’s artificial intelligence arm received the personally identifying medical records of 1.6 million patients on an “inappropriate legal basis”, according …
Data integrity, the next big threat
26 Nov, 2016The answer is very few. And Avellanet has the numbers to quantify his thesis: “Of the 20 data integrity audits that …
Recent Jobs
Do You Want to Share Your Story?
Bring your insights on Data, Visualization, Innovation or Business Agility to our community. Let them learn from your experience.
Privacy Overview
Get the 3 STEPS
To Drive Analytics Adoption
And manage change




